This question Pix belongs to the category “Protection and security: Securing the digital environment” and focuses on the specific roles of cryptography in the digital world. Find out in this article.
You can also find all our PIX test solutions by clicking on this link.
Which of the following are possible uses of cryptography? [Discover the answer]
Here's how the question looks on Pix:

Statement : Which of the following are possible uses of cryptography?
What is cryptography?
The cryptography is the art of protect messages so that they can only be understood by those for whom they are intended. The idea is to prevent the message from being read by curious individuals and therefore to write in coded. Only he who knows the secret key can decipher it.
It is based on several fundamentals:
- the encryption and the decryption
- cryptographic hash functions
- the authentication principle
Example :
Original message: “Hello”
Encrypted message: “Cpokvs”
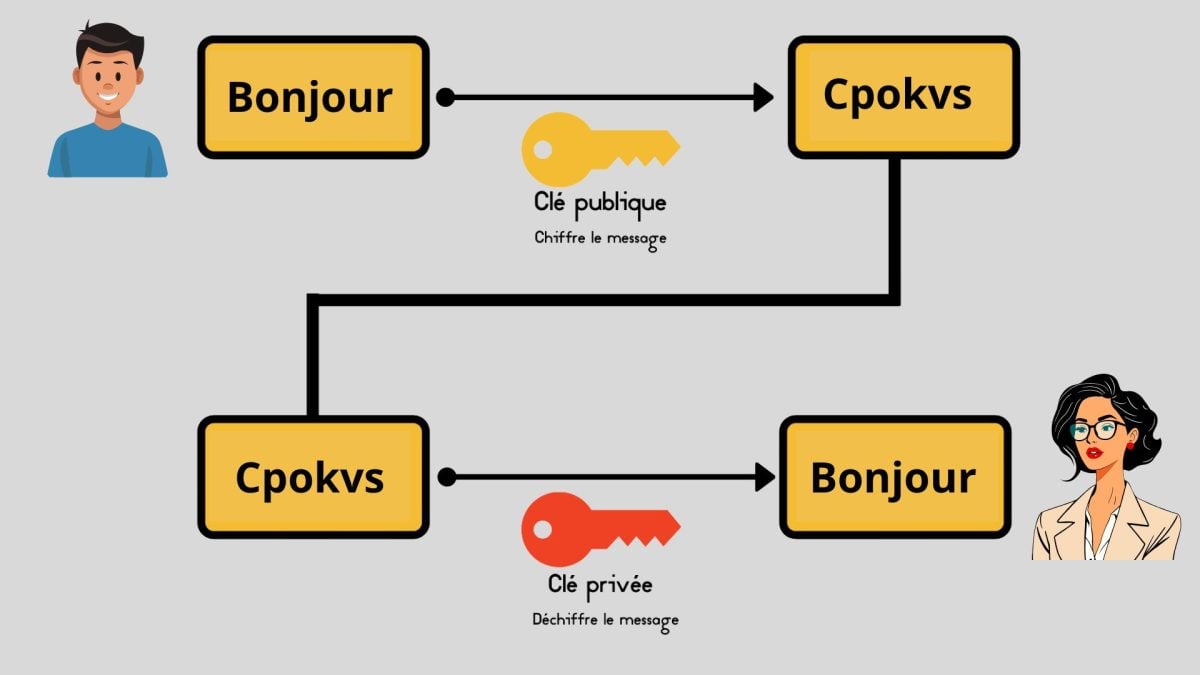
From a technical standpoint, cryptography is based on mathematical algorithms designed to encrypt and decrypt data securely. It uses keys according to asymmetrical methods :
- Public key for encryption
- Private key for decryption
For the symmetrical method, a same key is used for encryption and decryption.
In both cases, cryptographic mechanisms ensure that only authorized recipients can access encrypted data.

The cryptography is used in many IT systems to guarantee security. EFor example, it can be used to :
- Data protection on the Internet (e-mail, payments, passwords).
- Verify identity using a public key.
- Ensure that messages have not have not been modified using hash functions or digital signatures.
The following table lists key dates in the history of cryptography:
| Date | Event |
|---|---|
| Around 2000 BC | The Egyptians used modified hieroglyphs to hide the meaning of certain texts. |
| Around 50 BC | Julius Caesar created a simple coding system: the Caesar cipher. |
| 16th century | The Vigenère cipher is developed, making messages more difficult to decipher. |
| 1976 | Birth of modern cryptography with the idea of public and private keys (Diffie and Hellman). |
| 1977 | Creation of the RSA algorithm, still used today to secure data through encryption. |
| Today | Cryptography is everywhere: on the Internet, in our phones, on our credit cards, etc. |
What are the benefits and risks associated with the use of cryptography?
Cryptography is a very useful tool for protecting our data personal and professional. It is at the heart of computer security. But like any technology, it can also cause problems if misused or abused.
| Benefits (Avantages) | Risks (Disadvantages) |
|---|---|
| Protect your privacy personal and professional data. | Can be used by criminals to hide their activities (cybercrime, terrorism). |
| Ensures integrity messages (cannot be modified). | Makes certain police investigations more difficult (messages unreadable without key). |
| Enables authentication using a public key (verifies the identity of a user or website). | If a private key is lost Where flight, it becomes impossible to access the data. |
| Secure online payments and website connections using encryption (HTTPS). | Some methods can become obsolete over time or be vulnerable to attack. |
| Protects communications (email, messaging, VPN, etc.). | Can give a false sense of security if poorly implemented. |
In short, cryptography in general, whether it be symmetrical Where asymmetricalplays a central role in the DATA SECURITY and the communications protection digital.
To ensure optimal protection, it is essential to adopt a rigorous safety practices. It is possible to combine symmetric cryptography with other methods tailored to the specific needs of information systems.

What is Pix?
Pix is an online tool designed to help you better master the digital. Here you can answer questions on a wide range of topics: data and computer security, information retrieval and more.
The great thing is that the exercises adapt to your level as you go along. You progress at your own pace, and if you wish, you can obtain a recognized certification.
In conclusion, it is important to note that cryptography is used everywhere around us, often without us realizing it. It is essential for ensuring the computer security and protect data via encryption, using public and private keys.
And if you would like to continue practicing for the PIX tests, feel free to check out the following articles on our website:






