To remember:
- Common techniques for hacking an Instagram account in [year] include brute force, phishing, social engineering, and password guessing, with varying difficulties.
- Instagram account hacking is illegal, and this article aims to inform about account protection and recovery rather than encourage such practices.
- Legal solutions such as parental control apps are suggested to monitor activity on Instagram in a family setting, highlighting the importance of communication and consent.
The 4 techniques to hack an Instagram account in 2024?
Article checked and updated as necessary on : April 25, 2024
instagramcreated in 2010, is a photo and video sharing application. Account hacking on Instagram involves unauthorized access to a user's account, often by phishing or other hacking.
In this article, you will discover how to hack an Instagram accountwith the methods commonly used in 2024 and, how to recover an Instagram account after an account has been hacked. We've been reading hundreds of articles on the subject for some time now, so here's a summary of everything we've found on the Internet, as well as referent books on the subject of hacking.
Table summarizing Instagram account hacking in 2024:
| Technical | Difficulty |
|---|---|
| 🔍 Spyware | Easy |
| 🔐 Guess the CDM | Medium |
| 🎣 Phishing | Very difficult |
| 💥 Brute force | Hard |
Discover the best app to hack an Insta account in 5 minutes :
👀Discover the editor's choice👀
It's important to point out that hacking Instagram is illegal. It's a violation of other people's privacy. Our article is informational and aims to help anyone who needs to hack an Instagram account easily.
The software we recommend in this article is used to monitor the social networking accounts of children/adolescents, since it is a parental control application. As such, communication is crucial, in order to ask their permission beforehand.
How to hack an Instagram account: the 4 best techniques

In order to achieve your account hacking goal, you must use one of the methods that exist. Here's how:
Method 1: brute force
- In the old days, piracy required users to download a TXT document which contains frequently used and updated passwords on their browser.
- The browse this list trying out each password one by one, until it finds the perfect combination.
It can take a long time, and you can find out how many hours, minutes or seconds a brute force attack takes. Discover How long does it take to crack a password?
Brut force: effective and dangerous
In fact, this technique worked very well until other defense techniques came on the market:
- The special characters ;
- The generators random passwords ;
- Lauthentication with two factors.
Important update: These new methods have reduced the effectiveness of the brute force method. In addition, the social application has protected their site against this type of attack. As a result, this technique is no longer valid in 2024!
In the past, to hack the Instagram access code all you had to do was :
- To install software that was available on Github.
- Launch Tor
- Launch the software via Tor
- Enter user name
- Add access code list
- Expect
But now it doesn't work with the 2FA.
Method 2: Phishing
This technique is prohibited and requires code skills.
To do this :
- You need to be able to create a site that resembles Instagram and make sure that the person fills in their information (username and access code) and that AUTH security is not activated on their account.
- As soon as everything is created prepare an alert e-mail security code. This email should make it appear that the target has requested a password reset code on their profile, for example. And if they haven't, they need to change their access code on their profile, with a link to your pirate website.
- Once the information has been retrieved, you can log in.
On average, this costs 1000 € to create and it's not guaranteed to hack the target's Instagram account.
To use a safer and less expensive hacking technique:
🏴☠️Pirater an Insta account with EyeZy🏴☠️
Method 3: Social engineering
Social engineering is the art of manipulate people to disclose confidential information, on social media or otherwise. The types of information these criminals seek can vary, but when individuals are targeted, attackers often look for access codes or sensitive data such as banking information, etc.
Common techniques
The attacker invents such prepared scenario (or pretext) to obtain information from the target. For example, pretend to be a bank employee to ask for your account details.
- Sending e-mails that seem to come from a real source to trick recipients into providing sensitive data, such as IDs or credit card numbers, is known as phishing. As seen above.
- Baiting The attacker offers the victim something attractive to participate in. An example is free software that is actually malicious.
- Quizzing Use of fake quizzes or surveys to encourage people to provide personal information.
Note that when a person follows an authorized person into a secure area, such as a company building, certain terms are preferred, including tailgate or piggybacking.
Effectiveness of this technique
Social engineering exploits people's natural tendency to trust and want to help. Attackers can also push someone to act without thinking by using cognitive biases such as urgency (saying something is a "short-term offer").
In general, social engineering works, especially when the person wishing to hack your account tries to appear convincing and concerned for your welfare.
Preventive measures
- Education Training and awareness-raising are the first line of defense against social engineering attacks.
- Companies can set up protocols to verify the identity of anyone requesting sensitive information.
- Physical protection The company's commitment to safety and security includes the use of access badges for buildings, and training employees not to leave doors open to strangers.
Real-life examples and case studies
Kevin Mitnick and other famous hackers have used social engineering as one of their main methods to penetrate secure systems and networks.
Method 4: Instagram password guesser
Some hackers opt for this technique to hack Instagram. Usually, this is the technique used by parents to break into their children's social network using their cell phone.
Why do people use common passwords?
- Ease of memorization : Because they're easy to remember, many users choose simple access codes.
- Lack of education Some users are unaware of the risks involved in using weak or common access codes.
- Too many accounts : With the growing number of online services, many people find it difficult to keep a unique identifier for each account.
Illustration: the most popular and most hacked passwords
A table would show the most frequently used passwords, such as :
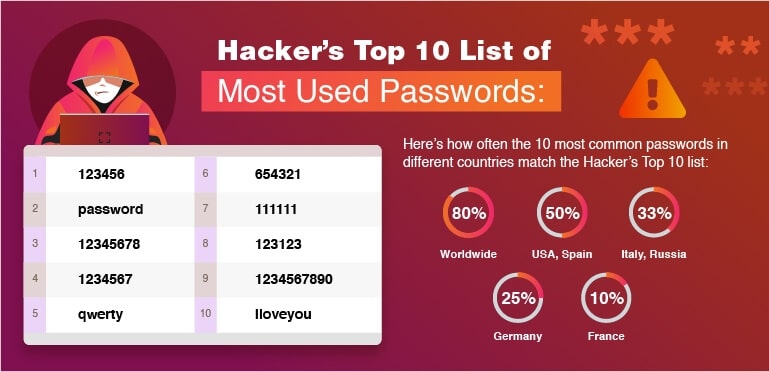
Common combinations:
Here is the password most used by users worldwide:
- 123456
- password
- 12345678
- 1234567
- qwerty
- admin
- azerty
- 111111
- iloveyoy
Using frequent passwords: the risks
- Brute force attack Attackers use software that tries thousands of passwords in a single second to gain access to an account.
- Damage to the dictionary : Hackers try to guess IDs using a file containing many common words and phrases.
- There were a violation of several accountss. If a user uses the same code for several services and one of them is compromised, all his accounts are at risk.
Having a strong Instagram password: Why is it crucial?
- More security More complex access codes are harder to guess or hack, making them more secure against unauthorized intrusion.
- Protecting your personal data A good secret code protects your personal, financial and other sensitive information.
- To avoid fraud : Strong access codes reduce the risk of identity theft and other types of online fraud.
Tips for obtaining a strong access code
- Use a mixture of letters upper and lower case, from figures and of special characters.
- Avoid use names, dates of birth, dictionary terms or other easily accessible information.
- Use a password manager to keep an eye on your passwords, and change them regularly.
Conclusion about guessing the password
Although there may be a strong temptation to use simple access codes, it's essential to resist this urge to protect your online information. You can significantly increase your online security by understanding the risks associated with weak access codes and taking steps to create more complex ones next time to avoid any kind of online hacking.
Method 5: Use apps to spy on an Instagram account
For parents, couples or people who are close to you, and those who want to monitor and spy on your loved ones' accounts: there's currently only one tool I recommend you try out, and that's EyeZy. EyeZy is one of the best parental control software programs out there, enabling you to keep a closer eye on the person you're monitoring.
Of all the tools on the market, we're confident in EyeZy's performance. It's an application that's perfect for seeing your target's messages and all their activities on social networks without them even knowing it, so test it out!
👁️🗨️Surveiller an Insta account with EyeZy👁️🗨️
How to hack an Instagram account with EyeZy?
To monitor an Insta account with EyeZy :
- First of all, go to this page to register:
- Next, choose the type of device you want to monitor;
- Now choose the type of plan that suits you best;
- Then validate the transaction by adding your payment details;

- The next step is to install the application on your child's cell phone. You'll need to have access to your child's or teenager's cell phone at this stage.
- Now you can easily access all your target's social networking activities and start monitoring with this application. All the necessary data on your target will be available through a user-friendly dashboard (SMS, text messages, photos, videos, social network exchanges, etc.).
For those who have lost their account and want it recoverThe tool above lets you do everything remotely on your phone, so even for yourself, I recommend installing it on your phone (I have it in case my phone or Instagram account gets stolen!).
Otherwise, the only way to get your account back is to request support and try to recover your password. Unfortunately there are no other solutions :(. Beware of other sites that try to scam you by calling phone numbers.
How to hack an Instagram account for free?
If you want hack Instagram for free without using the services of websites or platforms, you can use the forgotten password technique. However, you must have the information associated with the account, such as the telephone number or e-mail address. In this technique, we have chosen the mobile connection.
By having access to the target's cell phone:
- First access the ;
- Then go to the menu, go to "connection" and enter your target's mobile number;
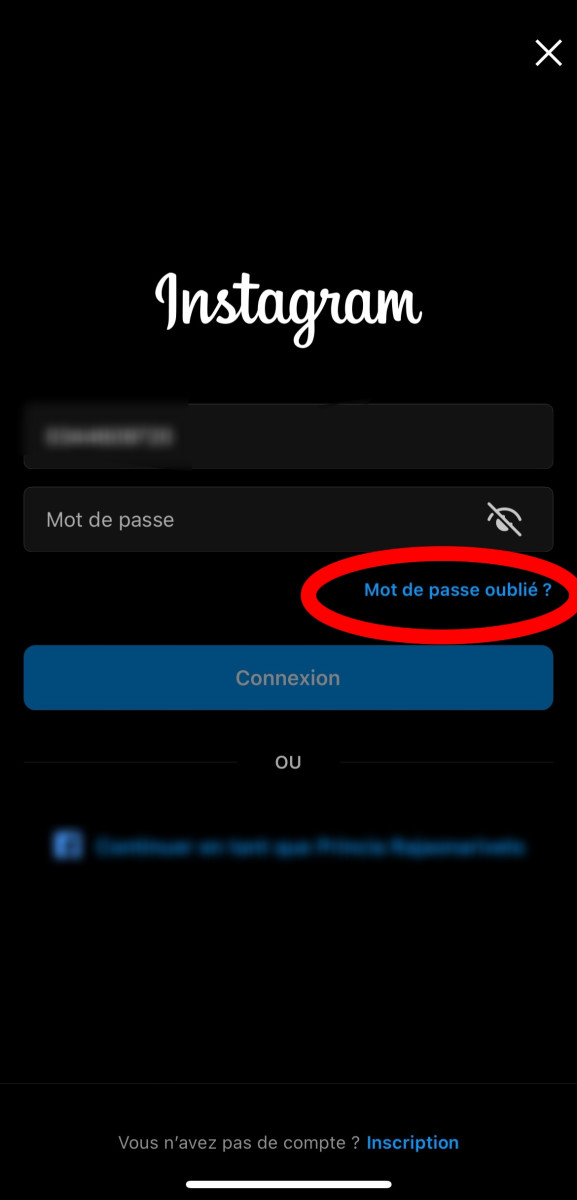
- Now click on "Forgot your password?
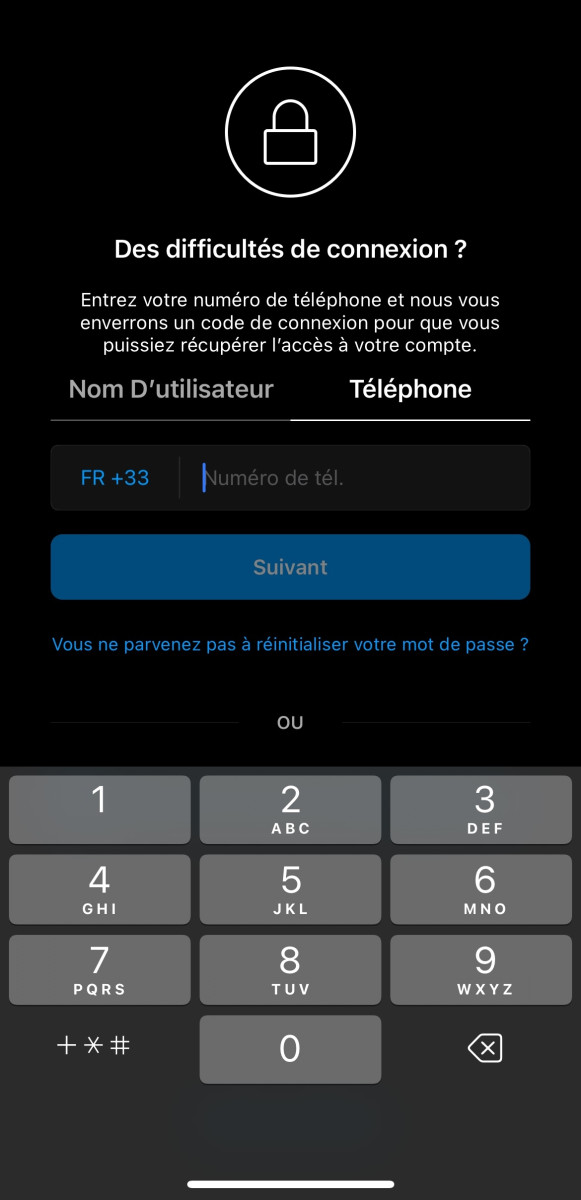
- Enter the target's telephone number in the field provided, then click on "Next";
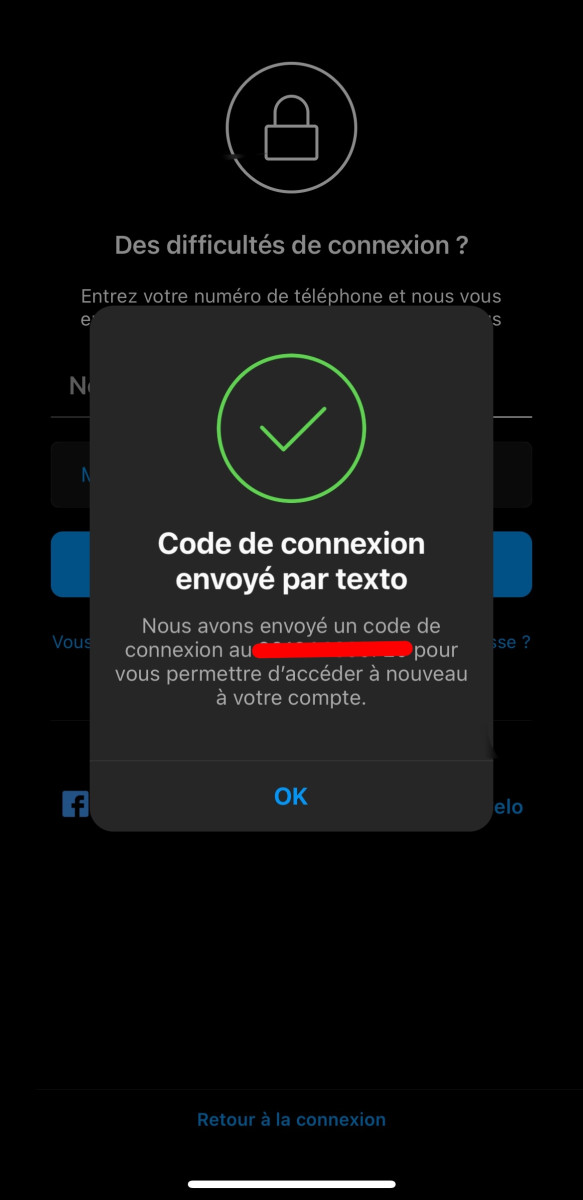
- By clicking on it, a login code will be texted to you, allowing you to access the account.
- After entering the code, you'll have access to the account and will be asked to reset the access code.
It's free, and requires no special tools!
Is it possible to hack an Instagram account without a password in 2024
In fact, it's possible to hack Instagram without an access code. The most common problem is forgetting, which happens to everyone. How many times have you registered online without physically writing down the access code?
Most users choose general access codes for several accounts. But this is the best way to get hacked. The hacker just gets it from one site, then tests it on all the sites he knows. But it also happens that you can find your access code by knowing the following information: Pet name, date of birth, etc...
But if you want to take action instead of guessing access codes :
👁️Pirater an Instagram account with EyeZy👁️
Answer to the question, is it possible to hack Instagram without having the password?
Currently it's not easy to hack Instagram without the methods above and without having installed the software I've put at the top or bottom of this page. I advise you to stop your searchbecause other sites want you to install viruses!
Some sites will offer you to download software, but to hack your computer. If there's a way to hack your account or another, we'll tell you on this page. So you can bookmark it, but it will be impossible or almost impossible.
What are valid reasons for hacking Instagram without using a password?
As mentioned above, hacking an account is a violation of privacy. But when faced with unavoidable contexts or personal reasons, it can be hacked. In particular :
- To check your child ;
- When the access code is forgotten ;
- You have lost your phone and bought a new one.
Whatever the reason, there are always effective ways of accessing the target's account. However, we don't advocate illegal spying, especially without the target's consent. Hacking is forbidden if the user becomes aware of it and lodges a complaint, proving that you are the perpetrator.
Instead of hacking an account to find out who's following the person, find out... how to see someone's latest followers on instagram without subscribing to his account.
How to recover a hacked Instagram account?
If you're worried that your profile has been maliciously intruded upon, or that you've lost it in the hands of the wrong people, you should know that there are various security procedures to help you reclaim your space. These procedures take a variety of forms:
- The first step is to take a look at the Instagram mails. Check the e-mails sent by the site's security department. To do this, go to security@mail.instagram.com. Here you can potentially find crucial information on the changes that have affected your account and cancel them if necessary.
- Option two is to retrieve a connection link. If access to your Instagram space seems hermetically sealed, requesting one from the platform remains one of the viable prospects. Just enter your e-mail address or phone number and follow the instructions.
- Then you can request a security code or Assistance. If you're struggling to remove your account from its perilous position, enhanced assistance can be engaged from a mobile terminal.
- A identity verification may also be necessary. This social platform can require confirmation of identity. This can be obtained by disclosing certain details, or by making a personal video recording for manual verification purposes. The video will be deleted after 30 days and will remain invisible to other site users.
- Finally, if access to your account is still feasible, or if you suspect that an intrusion attempt has been made but you are still able to access your profile, it would be wise to perform a change access code, ofactivate two-step authentication, of control your information and limit access to third-party applications of a dubious nature.
The primary function of each of these steps is to facilitate the recovery of secure access to the user's account. They aim to ensure that only the legal owner of the Instagram space holds the key to its use.
What's more, once a hacker takes control of your account, they'll have access to all your texts, photos, videos, and even influence your marketing strategy. Fortunately, the SMM panel for Instagram exists to help you stand out on this social network.
How do you protect your Instagram account from hacking?
- Use a strong access code It must be at least 12 characters long and contain a mix of upper- and lower-case letters, numbers and symbols.
- Pay attention to the links you click on If you receive an e-mail or text message from someone you don't know containing a link, don't click on it. The link may be malicious, and you could fall victim to phishing or be infected by malware.
- Keep your software up to date Software updates often include security patches that can help protect your computer or mobile device from malware.
- Activate authentication two-factor This option adds a additional level of safety to your account. When you activate two-factor authentication, you must enter a code on your phone in addition to your access code when you log in. We also encourage you to update your application to avoid the hassle of hacking.
If you need help recovering your Instagram account:
If you need help recovering your Instagram account, you can send an email to :
We'll get back to you within 48 hours to offer you customized assistance based on your requirements.
In conclusion
There are several ways to hack Instagram, but most of them are illegal and opposites ethics. Here are some methods you should avoid:
- Phishing This involves sending a fraudulent e-mail or SMS message that appears to come from Instagram. This often contains a link which, when clicked, takes the victim to a fake login page for the platform. If the target enters their login details on the fake page, the hacker will be able to steal them.
- Malware This involves installing malware on the target's computer or mobile device. The malware can then be used to steal the victim's login credentials or gain access to their account by other means.
- Social engineering The idea is to trick the target into giving up their login details or access to their account. To do this, the person can pretend to be a legitimate Instagram employee or create a convincing fake login page.
- The spyware on phones like Mspy and Eyezy, it's currently one of the easiest tools for hacking social networks!
So how easy is it to hack an Instagram account?
👀Pirate Instagram with Mspy👀 software.
It's important to note that these techniques in 2024 are illegal and unethical. If you're caught hacking an Instagram account, you risk legal consequences.
How and why did we write this article?
This top 4 was made after hundreds of hours of research and work, reading a maximum of information on hacking and books that you can find in the references just below. We wrote the article because a cousin wanted to hack an Instagram account after receiving a lot of insulting messages and wanted to find out who was behind her accounts. We couldn't find anything on the internet that answered the question of : How to hack an Instagram account. So we wrote this article to help all the people who were like us.
References :
- Andress, J. (2011). "The Basics of Information Security: Understanding the Fundamentals of InfoSec in Theory and Practice". Syngress. ISBN 978-1-59749-653-4.
- Downs, J., Holbrook, M., & Cranor, L. F. (2006, April). "Decision strategies and susceptibility to phishing". In Proceedings of the second symposium on Usable privacy and security.
- Mitnick, K. D., & Simon, W. L. (2002). "The Art of Deception: Controlling the Human Element of Security". Wiley. ISBN 978-0-7645-4280-0
- Florencio, D., & Herley, C. (2007, October). "A large-scale study of web password habits". In Proceedings of the 16th international conference on World Wide Web.
- Yan, J., Blackwell, A., Anderson, R., & Grant, A. (2004). "Password Memorability and Security: Empirical Results". IEEE Security & Privacy.
Other pages on our site to help you on your social network:
- How to hack a TikTok account?
- How to hack an Instagram account?
- How to hack a Facebook account?
- How to hack a Telegram account?
- How to hack a WhatsApp account?
- How to hack a Twitter account?
- How to hack a Messenger account?
- How to hack an Onlyfan account?
- How to hack a SnapChat account?
- How to hack a Youtube account?
- How to hack a Pinterest account?
- How to hack a Line account?







Quiero hackear la cuenta de mi novio @maximojara2 para ver con quien abla😠
is not a good idea ^^
Like
hermano puedes ayudarme con algo
In french pls 🙂
Necesito hackear la cuenta de una prima que falleció para ayudar a la investigación que está llevando a cabo.
You have to contact instagram support and it's the police who have to handle it
Hola, hackearon me la cuenta @ariella_ook , tengo acceso a mi correo pero pide me un codigo de respaldo que nunca configure en mí profile, al poner enviar codigo para cambiar contraseña me aparecen dos nros de celular que no son míos, y al final no hay manera de recuperar y la verdad tengo cosas important allí. Ayuda for favor
Hello,
can you send me more information about your hack in private? Maybe we can make a page to help those who get hacked 🙂
Is mia
?
Hola, podrías ayudarme? me robaron mi cuenta de Facebook, no se si puedas? 🙁
You need to send me more information
Necesito ayuda para recuperar la cuenta de una amiga
What ?
A ella le robaron la cuenta y están publicando cosas privadas su cuenta es guadita_aye
She can't ask for a new password by doing forgotten password? or by contacting instagram support?
Necesito ayuda para recuperar la cuenta de una amiga su cuenta es guadita_aye
Have you tried contacting support?
Necesito una mano par hackear una cuenta de instagra que está hablando a las muchachas mal y deprimiendolas,
No see xk lo hacen pero están jugando con la salud mental de las muchachas.
I think the best solution is to report the account 🙂
Estoy siendo acosada por @anabel_lao28 y me gustaría hackearla para borrar todas las photos que sube como yo. Lleva 3 años así 😢
Piracy is prohibited, if she puts photos that you do not authorize you can file a complaint
To hack
?
Me gustaria conseguir un dominio, la cuenta que lo tiene es como un bot, esta abandonada. Mi intention era hackearla y ponerme el number. Alguien ayuda?
did not understand everything
Poder ver que hace, habla mi hija, para tener un parental control sobre ella, ya que es muy problemática, y no quiero que tenga líos
How old is she ? it is better to talk to her about it and see what she does, forbid we will always find a way to override it, it is better to explain well
kız arakasımın ınsta sı var cala bılırmısın reıs
it's good what is insta right? She is free to do what she wants, right?
quiero si me podes hackear dos cuentas de instagram
Why ?
Me podrian hakear una vieja cuenta de instagram?me dan cringue mis viejas fotos.
Can you see by contacting support?
Mi esposo perdió acceso a su cuenta, se le blocó el celular porque cambio la contraseña y no recordó cual era
Can you have with support? 🙂
Quiero jaquear mi cuenta de instagram
Why ?
Quiero recuperar mi cuenta… No recuerdo la contraseña
Have you used another application?
Puedes hackearme la contraseña de la cuenta de mi pareja
why?
Necesito ayuda para hackear la cuenta de una chica con la que voy a iniciar una relación porque tengo una sospecha y si es cierta para evitar problems
What ?
Hola quiero jaquer esta una cuenta de Instagram pk quiero saber si tiene fotos de mi hija en la redes sociales
Have you watched Mspy?
necesito que me hackees mi cuenta de instagram que me la robaron ayer, o simplye eliminarla definitivamente, intende de mil maneras pero no funciona, ayudame porfa
You see the Mspy link? 🙂
Hola, llevo un mes tratando de recuperar una cuenta que me hackearon, cambiaron toda la información y Instagram no me ha dado ninguna solución, me podrían ayudar? 🥺
Did you install Mspy before from our link?
Ola kisiera hackear una cuenta de instagram ya k están usando mis datos y mis fotos personales para promocionar citas xxx espero me puedan ayudar
Have you contacted support?
hola necesito hackear una cuenta que demande que la pague dinero y me esta amenazando con publicar photos mias y enviarselas a mis familiares y amigos. es urgent, por favor
Send me an email asi resolvemos esto por favor necesito ayuda
More information please
Pls I changed my email on my Instagram and got logged out immediately. I don't have password to my page. I open my account through my Facebook page. Pls I need your help 🙏
Have you tried: https://www.alucare.fr/MspyInsta
Which tool we have to install in android in order to hack someone's Instagram account
https://www.alucare.fr/MspyInsta
La Netaa quiero hackear la cuenta de mi ex!! jajaja solo quiero saber so dirty con alguien mas
Have you thought about monitoring his account?
https://www.alucare.fr/MspyInsta
Quiero hackear una cuanta de instagram de un iphone como hago?
if you have access to the account:
https://www.alucare.fr/MspyInsta
hola, necesito una cuenta o que me den su contraseña- ya que ese tipo me hizo mucho daño así que por favor ayúdenme soy una chica en problema-…que no quiere ser expuesta a problemas cybernéticos o que me ayuden a hackear
What ? 🙂
I want to hack someone account
its prohibited ^^
Account was hacked and every password, email and phone number was changed… if anyone knows how to help I'd be much appreciated
You contact the support team?
un muchacho me esta amenzando con undergo fotos mias o venderlas tengo miedo ayuda soy menor de edad
Need more information
Pls I need your help no my Instagram account . I don't have access to it anymore
you have taken Mspy before?
I like the hackeo topics and the detection of vulnerabilities in the computer systems. recientemente he estado practicando un poco con las computers de mis amigos, claro ellos no lo saben, mi novia pelea conmigo porque dice que eso es malo. ademas, mi jefe tambien es un poco obsesivo con estos temas y me esta pagando para hacer este tipo de trabajos. creo que necesito un consejo, me pueden ayudar?
What ?
Hola como podría contactar contigo??
go to https://www.alucare.fr/MspyInsta
Hello, I forgot my Instagram password could you tell me how to hack my account on ios or windows please
You dont take Mspy before?
No i didn't and i can't afford it
we dont have other solution 🙁
Hello I lost my phone and can't remember the email or password i only know about name of my insta account please help i want it back
you have installed Mspy before?
Tienes link para descargar?
Yes 🙂 https://www.alucare.fr/mspyinsta
porfa me han hackeado mi cuenta de instagram, me cambiaron el correo electronico el numero de telephone y lo borraron de facebook que puedo hacer.
you have installed Mspy before?
Me paso exactamente lo mismo el viernes y no he podido recuperar mi cuenta, de casualidad pudiste hacer algo por la tuya?
You need to install Mspy before: https://www.alucare.fr/MspyInsta
If you have mspy in your phone before, you can see your account 🙂
Meu Instagram faith hackeado já tem owe dias eu quero minha conta de volta
did you follow the tutorial?
Hello. Creo that you quedó the most important. Hackear una cuenta que ya te han hackeado previamente, para recuperarla. This creo is the most important. Y he de añadir que hay que tener mucho cuidado con los estafadores que se hacen pasar por hackers y lo único que buscan es el beneficio propio. Lo digo por experiencia
Yes, its for that you need to take care 🙂
Hello,I want an instagram user's mobile number,but I don't want to notify him that I got his mobile number.How I do that .Pls help, it's very urgent
Check here: https://www.alucare.fr/MspyInsta
I want hack a insta very old close account if u can help me reply me
You have read?
Hello,I want an instagram user's mobile number and email address ,but I don't want to notify him that I got his information .How I do that .Pls help, it's very urgent
you cant if you dont use mSPY in the phone of this guys (but i think you cant use)
Skal man bruge oplysninger på den andens telefon for at kunne bruge mspy?
Yes
i need mspy free
I am very grateful to the Mspy company I was able to spy on the instagram account perfectly
Nunca la probé y espero sirva 😊
Bueno eso es todo bye byeee🌼🧡
Hello,
thank you again for your article, it's the only one that has allowed me to understand everything and explain it completely, I no longer have any questions on the subject!
I have a 15-year-old who spends most of her time on Instagram. I'm starting to worry about the things she shares or receives privately.
Thanks to your article, I was able to enter her account and do some checking on what she exchanges.
Thank you for your advice and for this article
Hello,
I find your article particularly instructive in that once I know how and why my Instagram account can be hacked, it motivates me to make it even more secure.
Thank you for this article.
Gérald H.
Hello,
I created an Instagram account as a test. And I'm glad to hear that all the information you shared in this article is true.
Both EyeZy and MSpy are very easy to use, with just a few clicks.
Thank you for your research, your sharing and for your article.
Val
Hello,
Thanks to your article "How to hack an Instagram account", I understand better now Why some of the background.
It's certainly not just a question of sick jealousy, but also a way of reassuring, confirming and, yes, somehow protecting yourself from certain harmful relationships.
Even though the term hacker generally has a pejorative connotation, using it in the context of social networks like Instagram, really does help to protect yourself.
Thank you for your article.
Gaby
Hello,
Before reading your article, I thought that the most difficult step was to hack the Instagram account of a 16-year-old. Despite the fact that your article is very clear and therefore, easy to follow, the hardest part is telling that same person to be careful with everything they see, send or receive on this platform.
I think raising his awareness is a different kettle of fish. That said, thank you for your very informative article.
Yann
Hello,
I agree with the previous comments.
Your article is instructive in that it gives us a modicum of control over what our teens are really exchanging on Instagram.
At least, by hacking into their account we'll be able to act before it's too late.
Lis
Hello,
I found your article more or less informative and even tempting. I don't really know anything about the subject, but reading it makes me want to try a little hacking.
Mario
Hello,
Thanks to your article, I understand better now Why some do it.
It's certainly not just a matter of sick jealousy, but it's also a way to reassure, confirm and yes, somewhere to protect yourself from certain harmful relationships.
Hi,
Hacking usually has a negative connotation, but sometimes it allows us to control what our loved ones see and share as information.
Honestly, I'm hacking into my son's Facebook account for security reasons, and your article helped me a lot in knowing how to go about it. I feel much calmer now.
Thank you for your article
Hello,
I particularly liked the part about passwords.
When we create an account, we tend to forget that the password is for our own security, but sometimes we make a very easy one, which hackers can crack in less than 5 seconds.
I was a bit puzzled when I read your article, but I really enjoyed it... If you could also add some text on how to secure your instagram account.
Just kidding, thanks for your research and sharing.
Thank you very much, your article will help me a lot for new experiences 😉
Hello,
It's both a shame and completely understandable that hacking an Instagram account should be prosecuted and punished.
On the one hand, it's true that it's about getting into people's private lives. But on the other hand, reading your article, it would seem that hacking an account can be used to protect oneself, both against any outside attempt, but above all to protect our loved ones against the things they might see there.
Thank you.
Stephen
Hello,
Thank you for your comprehensive article.
Having said that, I wonder, is there any way for the "victim" of piracy to recognize who the perpetrator is?
I mean, if I'm (seriously) considering hacking someone's Instagram account, can that person know it's me?
Thanks
Hello,
I had my doubts about social engineering, in fact, I didn't even know the technique had a name.
Thanks to your article, I now know that under no circumstances should we divulge our personal information. Sometimes, it just starts with common questions like first and last name, then, one thing leading to another, they end up accessing all our personal information.
Thanks again for your comprehensive article.
Roro
Hello,
Thank you for your interesting article.
I had a lot of fun trying to hack my Insta account using your methods. Great stuff.
Ludo
Hello,
I had mistakenly thought that hacking an Instagram account required advanced programming knowledge or other computer skills.
Thanks to your article, I was able to hack an account, using the software you suggested. I can assure you that my intentions weren't bad per se, it was just for fun, but I loved it.
Thanks again for your very interesting article.
Yes, be careful, what I put in the article is not to do anything illegal with it!
Don't worry, I hacked my own account. It's a bit of a crazy idea, but it's all in the name of understanding the different possibilities.
🙂
Hello,
I used to think that the most difficult step was to hack the Instagram account of a 16 year old teenager. Despite the fact that your article is very clear and therefore, easy to follow, the most difficult to tell him that I hacked his IG account for his own safety.
I think making him aware of it is a different kettle of fish. That said, thank you for your very informative article.
S.
Hello,
Your account allowed me to access my daughter's Instagram account. Obviously, I had to do it behind her back because her behavior became strange overnight. I was able to find out that she was being bullied at school.
I don't know if his high school will consider my request, since piracy is still illegal.
In any case, thank you for your article.
Hehe,
Excellent article... I don't want to be a wet blanket, but it does make you want to try some illegal things.
No, I'm just kidding. At least I know what piracy is really made of.
^^
Great article... Even if it puts a few ideas in my head to take over my guy's insta account.
😈
Great article!
Well detailed, you can see that research has been done! Great
Hola, necesito recuperar mi cuenta de instagram a la que le cambiaron el correo electrónico y la contraseña porfavor, gracias
Looking for a way out? It's simple, When it comes to tracking Locations of cell phones, computer system & individuals using them or remote mobile hacking into devices, your article its perfect!